Team 6
A comparison study on wireless packet sniffers
Shabnam Kousha, David Lopez
I. Introduction
The usage of Wireless Local Area Networks (WLAN) has increased impressively in the recent years. Such is the increase, that almost all wired networks have been substituted for wireless ones, mainly in a domestic or public environment. However, wired LAN networks are still used in when the performance factor is essential. This project is focused on the analysis of different wireless sniffers[1].
Due to the evolution and dominance of the WLAN in nowadays networks, the use of this type of packet sniffers and analyzers is required to improve the security and performance of the cited networks. Not only security issues or performance improvement are in the scope of these tools, troubleshooting as well becomes easier when using these sniffers in the network being analyzed. So, Why do we need these tools, what do they do? The main functionality of a sniffer tool is to convert the data (binary) contained in the packets to a format that is readable and hence analyzable by humans. The tools ability to sniff, convert and analyze the wireless signal is commonly used by hackers in a malicious way. They can obtain passwords and relevant private information if it is not properly secured and protected. For that reason among others, knowing how to use packet sniffers to avoid and prevent these attacks to the network is crucial[2].
There are two types of wireless scanners modes, active and passive sniffing. An active sniffer will send probes out to the network and will wait to receive a response, then, the analysis is done by observing these responses. They have the advantage of being handy and useful providing link features but, they can’t sniff a closed network since they need to be associated with network object of the scan. In the other hand, a passive sniffer is much more dangerous due to its ability to eavesdrop a network. They change the network card mode to RF-monitoring and then passively sniff all traffic in a network.
We present in this review a group of wireless sniffers. We analyze their features, characteristics, applications, etc. A comparison between them is also done and finally we go through a case study with a real application to show how this software could be used to analyze a real world network[2,4].
II. Packet Sniffing Tools
Kismet
Kismet is one of the most commonly used wireless sniffing tools. It works as an 802.11 wireless dectector, and allow to any card supporting passive monitoring (RF-mon) to sniff any of the 802.11x standard specifications network. It contains all basic features such as displaying ARP and DHCP traffic, to save files in both Wireshark and TCPDump format and display level of activity at some different channels. It is able to measure and decode the traffic signals in real-time. For this ability, Kismet is one the most common software used by hackers. Since they can just go around any network and sniff the transmitting information. But, Kismet is not only use for hackers. It is one of the best software for intruders’ detection. The tool allows the identification of those users that are sending requests but never connecting to the network. It can be run in Linux and MacOS[3].
Snoop
Snoop is a simple and useful packet capture tool based on command instructions. It was developed by Sun Microsystems to work with Solaris OS. It displays the information in both single and multiple line formats. Snoop tool is able to sniff IPv4 and IPv6 packets. It is usually compared to TCPDump due to similarities in the way output data is displayed and formatted, being both tools almost identical in this feature. Just like Kismet does, snoop format could be changed to that of tcpdump or wireshark. Snoop is considered more efficient than TCPdump since it possesses all its capabilities and a much friendlier user interface. . In the other hand, snoop has some disadvantages. First, it has the issue of non-reassembling IP fragments, a feature which is not implemented in Snoop. A big limitation to only Sun systems due to its implementation on Solaries kernel is the main disadvantage of this excellent packet sniffing tool.
Wireshark
Wireshark, which was previously called Ethereal is the first public packet sniffing tool developed by Gerald Combs in 1997. Regardless of its name, it’s the world’s most popular free network packet sniffer and analyzer. Now, this tool is released under the GNU General Public License version 2 and it has been maintaining by a global team of protocol experts. It is compatible with different types of Unix-like operating systems like Linux, Solaris, FreeBSD, OpenBSD, and Windows OS. Moreover, since it has a graphical user interface, to help the user in navigating the capture, filter and analysis of packets, it’s very user-friendly.
Currently, the tool is used for network analysis, troubleshooting, intrusion detection, developing software and communications protocols, and education purposes. Like the other sniffing tools, it can also be used for malicious purposes. It can capture traffic and decode the messages to an understandable format for the user to find the reasons of poor performance, intermittent connectivity, etc. Wireshark can also log files (hourly, weekly depends on set up) to be analyzed later. The log files can be transferred from fast processing node to a slower analyzing system; as a result of this offline analysis there will be less message capturing lost as well as more performance for Wireshark.
The log files can be exported into different understandable formats from ASCII format to plain text, post script and CSV. This tool is very flexible as open source software to let network administrators add desired functions of intrusion detection in it. For example, the sniffing tools do not have any mechanism to check the pattern of the traffic and find intrusion or problem on the network and generate alarms. Instead there are lots of applications designed to be used with Wireshark to control the network pattern and take desired actions. Therefore, the flexibility feature of this Wireshark just allows us use different applications with it [3,4].
TCPdump
TCPdump is one of the free common network monitoring and debugging tools for TCP/IP packets. It was originally developed by a research team at the Lawrence Berkeley National Laboratory in 1990. It let the user to intercept, capture and monitor TCP-IP and other packets being transmitted in a network. This tool is compatible with most Unix based operating systems such as Linux, Solaris, BSD, Mac among others as well as Windows OS.
It is command line based software to capture, filter and log the packets using the users input rules; the output can be saved in a separated file which is not easily understandable for the user. Therefore, there are lots of freeware like Wireshark to be added to TCPdump to display the row data in an easy to understand format in GUI. However, some basic information such as timestamp and the protocol headers information contained in a frame can be showed in different line of the command page. In order to decrease the message drop using the TCPdump software, the analysis feature has been removed. Thus the software just works as a traffic capturing tool not an analyzer. There are lots of free software to do the analysis on the captured row data from TCPdump such as tcpdump2ascii and tcptrace among others. Using the filtering feature of this software we can limit the traffic being captured and logged. Thus, instead of looking for the desired packed in a huge number of packets we can have only the desired packets in log file [4,5].
III. Comparison and Contrast
A. Wireshark vs. TCPdump
Contrast:
1. Wireshark has user friendly graphical user interface:
- Displays information inside the packet in a meaningful format
- Well designed, thus even a newbie can understand captured packets.
- Makes the learning process easier and more interesting. On the other hand TCPdump does not have any graphical user interface
2. Wireshark displays the whole data inside the packet but TCPdump only shows information on packet headers, it does not display all the data inside the packet.
- TCPdump is less intrusive than Wireshark.
- For educational systems, using Wireshark in the lab is not legal for the students because they can easily see some confidential information like passwords for some protocols such as ftp, telnet, and pop3 but it’s not able to show information from Secure shell communication[2].
- Makes the learning process easier and more interesting
3. TCPdump can only show the information of TCP/IP based packets and does its job well. While Wireshark is much more versatile and can interpret and show different protocols.
- Wireshark can read TCPdump binary output and also use TCPdump filters to selectively capture or display records[3].
- It’s harder to learn TCPdump and its filtering rules rather than; because the rules of TCPdump may first appear completely cryptic[3].
- TCPdump has problem with some commands working with IPv6 packets; As a result, IPv6 users should use Wireshark.
- 7-Attackers have been able to send corrupt packets to make TCPdump crashed; although there are some remedies to fix such issues once found, it cannot be guaranteed that more of these vulnerabilities do not exist.
Similarities
- They both are compatible with different types of operating systems such as Linux, Solaris, FreeBSD, NetBSD, OpenBSD, Mac OS X, other Unix-like systems, and Windows.
- Like Wireshark, TCPdump also has a good filtering language to capture only the desired packets that match a specified filter.
- Neither Wireshark nor TCPdump function as an intrusion detection system.
- They both cannot generate alarm and hint when an active or passive attack or strange behavior happens. However, they might help the analyst find out what is really going on inside the network.
- There is lots of free software for both of them to analyze the packet and check the strange behaviors and intrusion detection [3].
- Both of them can only be used to measure or capture information. They cannot manipulate data on a network.
- They are not able to send massage in the network or do active things [3].
- The captured file format in both of them is “libpcap” format
Wireshark vs. TCPdump
Contrast:
- There are more than 500 app. protocols that Wireshark is able to decode while Kismet can only decode simple traffic such as FTP, HTTP, etc [1,4].
- Wireshark is abile to analyze dumpfiles. it can filter out interesting packets or data stream. It can also give statistics of some protocols such as TCP, HTTF while Kismet cannot do that [1,3].
Similarities
- They both are compatible with different types of operating systems such as Linux, Solaris, FreeBSD, NetBSD, OpenBSD, Mac OS X, other Unix-like systems, and Windows.
- Like Wireshark, TCPdump also has a good filtering language to capture only the desired packets that match a specified filter.
- Neither Wireshark nor TCPdump function as an intrusion detection system.
- They both cannot generate alarm and hint when an active or passive attack or strange behavior happens. However, they might help the analyst find out what is really going on inside the network.
- There is lots of free software for both of them to analyze the packet and check the strange behaviors and intrusion detection [3].
- Both of them can only be used to measure or capture information. They cannot manipulate data on a network.
- They are not able to send massage in the network or do active things [3].
- The captured file format in both of them is “libpcap” format
Wireshark vs. TCPdump
Contrast:
- There are more than 500 app. protocols that Wireshark is able to decode while Kismet can only decode simple traffic such as FTP, HTTP, etc [1,4].
- Wireshark is abile to analyze dumpfiles. it can filter out interesting packets or data stream. It can also give statistics of some protocols such as TCP, HTTF while Kismet cannot do that [1,3].
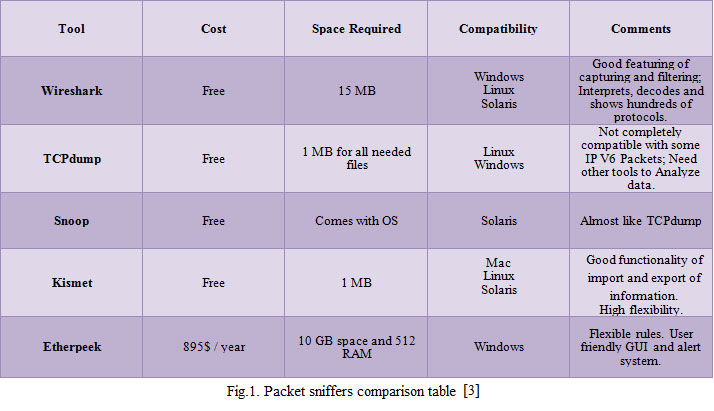
IV. A Case Study of Using a Packet Sniffing Tool [4]
Once we have fully explained some of the best and most commonly used packet sniffing tools we propose the procedure and methodologies for a network analysis. The procedure will differ depending on the network size and usage. If the WLAN being analyzed possesses a large structure, steps such as collecting traces from the router and authentication log are followed. Differently, if the network is smaller in scale, the use of the packet analyzing tools explained on this project suits the requirements in a better way. The usual steps include data collection and data analysis.
Data Collection
To determine which tool is going to be used, the analysis requirements and the system network under the scope need to be studied. All kismet, snoop, tcpdump and wireshark tools have the wireless packet capture feature. If the system uses a Solaris OS, then snoop will be the chosen software, Wireshark is the best and easier tool for Windows OS and for any system running under unix, both kismet and tcpdump will suit perfectly.
Data Analysis
The data collected will be analyzed and all the statistics will be obtained in the process. We could use the tool to filter the relevant data, TCP, UDP, etc, etc, depending on the analysis of interest. The main objective is to extract as much information as possible from the collected data in order to assess network performance, security issues and to perform a fast and efficient troubleshooting. The user’s behavior, network traffic, distribution across access points are very frequent metrics for these analyses.
V. Conclusion
In today’s world and technology, network performance cannot be ignored. It can be considered as a part of administrator life. Each administrator needs to monitor and analyze traffic packets to analyze the performance of a network. Thus, using network monitoring tools is inventible. In this paper different monitoring tools have been compared and contrasted. Using the comparison and contrasted information, the administrator pick the best work fit his/her job [2,3].
VI. References
- Usha Banerjee, Ashutosh Vashishtha, Mukul Saxena- Evaluation of the Capabilities of WireShark as a tool for Intrusion Detection- September 2010- International Journal of Computer Applications.
- Felix Fuentes, Dulal C. Kar- ETHEREAL VS. TCPDUMP: A COMPARATIVE STUDY ON PACKET SNIFFING TOOLS FOR EDUCATIONAL PURPOSE- 2000, In Texas A&M University-Corpus Christi Research Center.
- Feng Li, Mingzhe Li, Rui Lu, Huahui Wu, Mark Claypool and Robert Kinicki- Tools and Techniques for Measurement of IEEE 802.11 Wireless Networks- 2006- Modeling and Optimization in Mobile, Ad Hoc and Wireless Networks, 2006 4th International Symposium
- Travis Keshav- A Survey of Network Performance AnalysisTools- Project Paper
- Nguyen The Anh, Rajeev Shorey,- Network sniffing tool for Wlans: Metric and limitations- 2005- International conference on Signal Processing Systems, Singapur